Find critical vulnerabilities in minutes. No code. No setup. Just paste your URL.
FeedBugs performs external security scanning of your website, SPA, or API, uncovering vulnerabilities in security headers, TLS configuration, CORS, authentication flows, XSS, SQL injection, sensitive endpoints, API security, and third-party dependencies.
How FeedBugs Works
Assess your website's security with a streamlined, step-by-step process.
Enter Your URL
Just type your website, SPA, or API endpoint. FeedBugs supports HTTPS, subdomains, and custom ports.
Domain Verification
Before scanning, FeedBugs confirms you own or manage the domain through DNS TXT record or meta tag verification. This protects your domain from unauthorized scans.
Security Scan
FeedBugs launches all scanners in parallel — checking for XSS, SQLi, CSRF, security headers, SSL/TLS, CORS, authentication weaknesses, and more.
What we scan for
Feedbugs runs a deep set of automated checks across your app, APIs and infrastructure-facing endpoints.
Security Headers
Validates X-Frame-Options, X-Content-Type-Options, HSTS, CSP, Referrer-Policy, Permissions-Policy and more.
SSL/TLS Security
Checks certificate validity, protocol/cipher strength, HSTS configuration and HTTPS best practices.
Cookie Security
Analyzes cookies for HttpOnly, Secure, SameSite, scope, lifetime and presence of sensitive data.
CORS
Detects overly-permissive CORS rules, wildcard origins, dangerous headers and missing preflight support.
XSS Detection
Tests for reflected and DOM-based XSS using context-aware payloads and scans for dangerous sinks.
SQL Injection
Sends safe SQL payloads and looks for error messages, response anomalies and timing differences.
Authentication
Discovers login/auth flows, checks HTTPS, CSRF, rate limiting, error messages and logout behavior.
Broken Access Control
Probes sensitive endpoints, IDOR patterns, path traversal and unauthenticated access to admin APIs.
API Security
Detects REST/GraphQL APIs and checks auth, rate limiting, pagination and sensitive data exposure.
Clickjacking
Verifies X-Frame-Options or CSP frame-ancestors protection and detects legacy frame-busting scripts.
Information Disclosure
Looks for stack traces, debug flags, internal URLs, version leaks, console logs and exposed API keys.
Mixed Content
Finds HTTP resources (scripts, styles, images, iframes) loaded on HTTPS pages, including via CSS.
Open Redirects
Tests common redirect parameters and OAuth flows for unsafe redirects to external domains.
Rate Limiting
Sends controlled request bursts to detect 429 responses, Retry-After headers and limit thresholds.
Dependencies / JS Libraries
Inspects package manifests and frontend libraries for outdated or risky versions and missing SRI.
Secrets Exposure
Scans HTML, JS, JSON and source maps for embedded secrets, API keys, tokens and credentials.
security.txt
Checks for a valid /.well-known/security.txt file with Contact, Expires and recommended fields.
Sensitive Endpoints
Probes for exposed .git, .env, backups, config files, admin tools, API docs and framework-specific paths.
Subdomain Takeover
Looks for subdomains pointing to unclaimed resources on providers like GitHub, S3, Netlify or Vercel.
Features
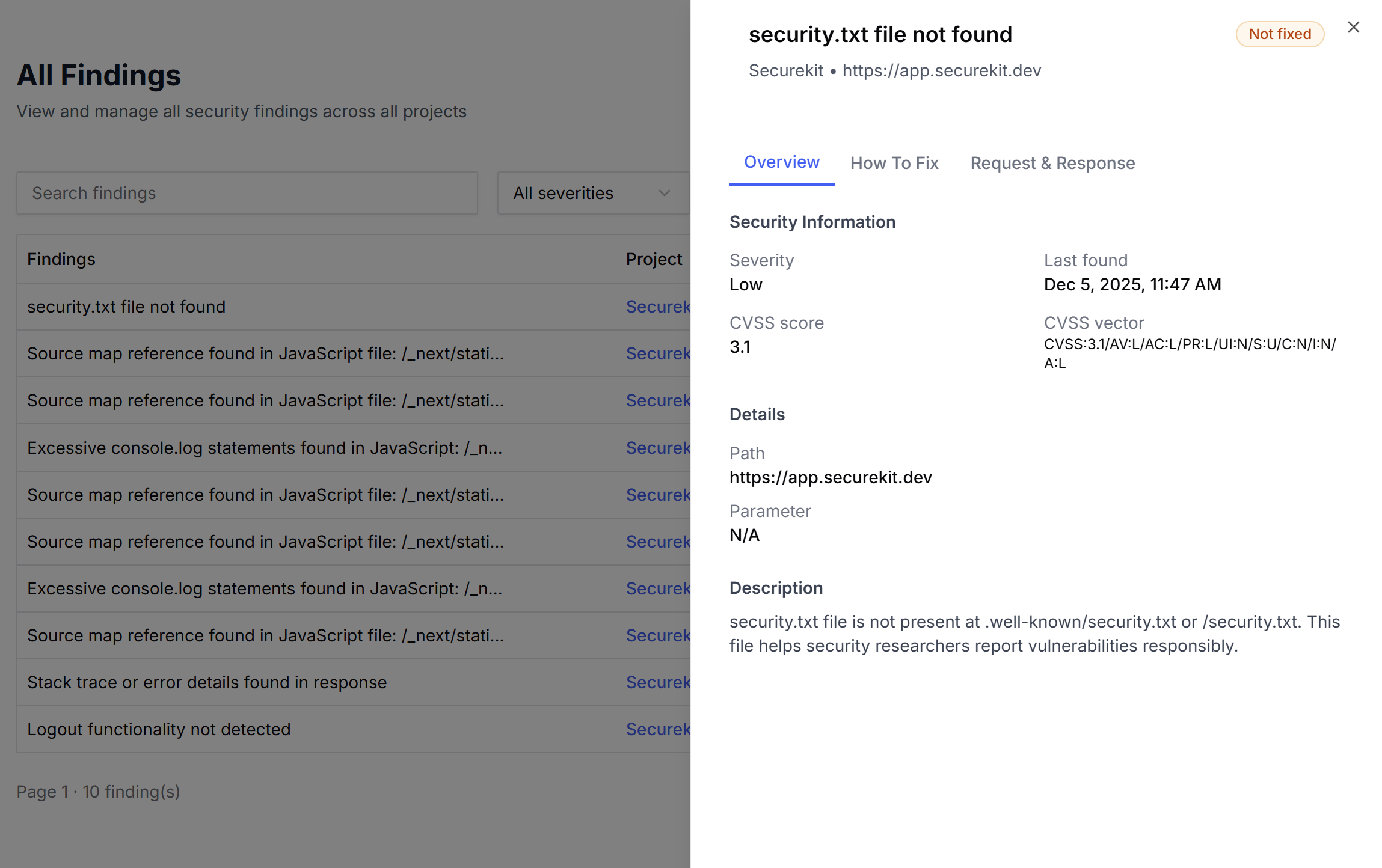
All Findings
View and manage all security findings across all projects.
Search & Filter
Quickly find specific findings using search functionality and filter by severity levels (Critical, High, Medium, Low, Info) to focus on what matters most.
Detailed Analysis
Each finding includes severity levels, CVSS scores, technical details, and exact remediation steps. Get everything you need to fix issues fast.
Actionable Insights
View findings with clear descriptions, affected paths, parameters, and step-by-step fix instructions. Engineers get technical details, founders understand risks.
Project Overview Dashboard
Get a comprehensive view of your project's security status at a glance with real-time insights and detailed metrics.
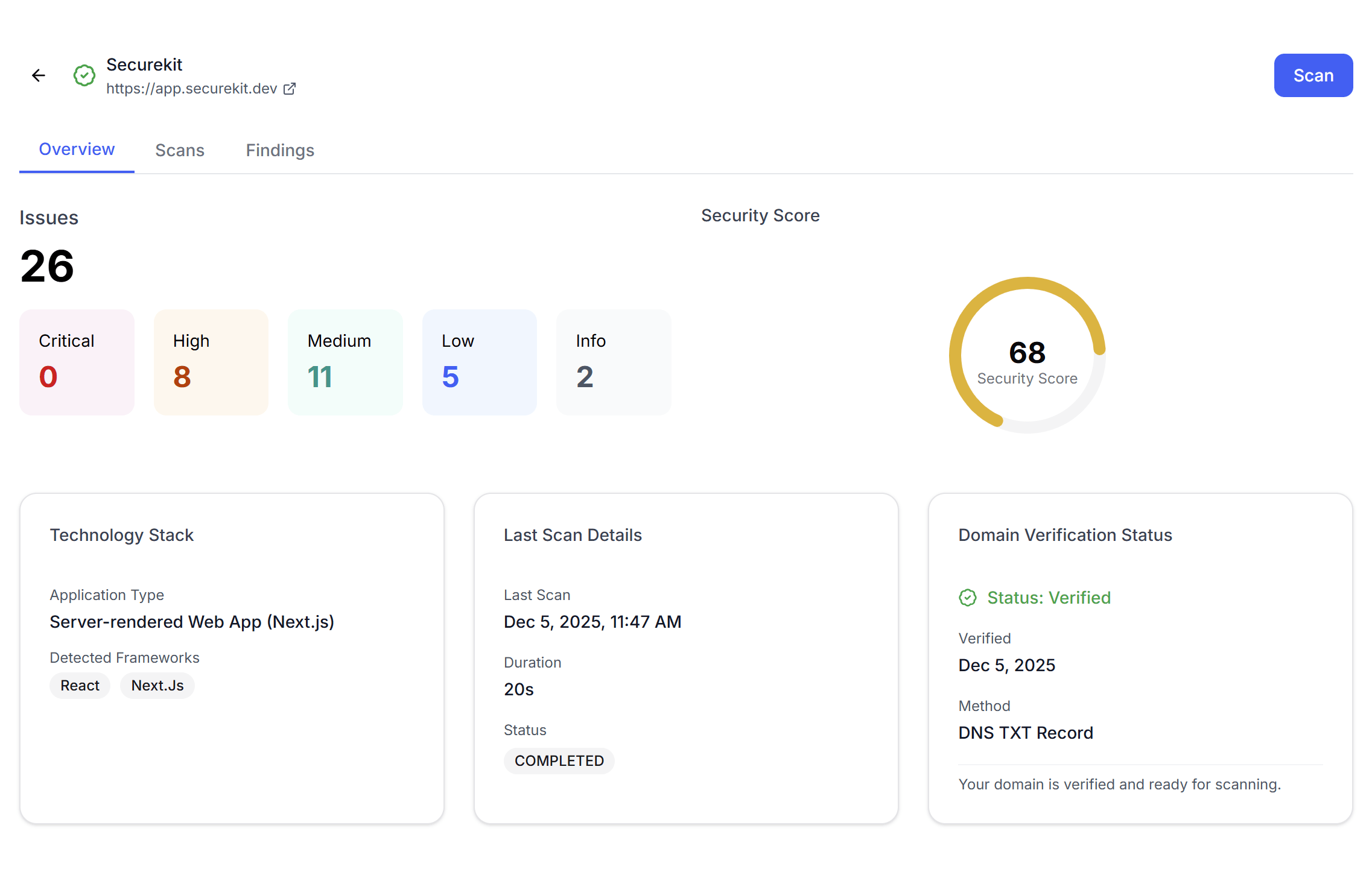
Issues Breakdown
See all vulnerabilities categorized by severity with color-coded indicators for quick assessment.
Security Score
Visual gauge showing your overall security posture based on all detected vulnerabilities and their severity.
Tech Stack Detection
Automatically identifies your application type, frameworks, and technologies to run relevant security scans.
Pricing
Simple, transparent pricing. No surprises.
FREE
Perfect for testing - Get started with essential security checks
Free
- 1 project
- 1 scan
- Security Headers check
- SSL/TLS Security audit
- Sensitive Endpoints detection
- Information Disclosure check
- Clickjacking protection test
- security.txt detection
- 7-day scan history
STARTER
Professional security for indie developers and small teams
$19.00/month
- 5 projects
- 50 scans
- 30-day scan history
- Everything in FREE, plus:
- XSS vulnerability testing
- SQL Injection detection
- Authentication security checks (CSRF, CAPTCHA)
- CORS configuration audit
- Cookie security analysis
- Open Redirects detection
- Dependency vulnerability scanning
- PDF reports
- Email alerts (coming soon)
PRO
Enterprise-grade security with unique threat detection
$49.00/month
- Unlimited projects
- 500 scans
- Unlimited scan history
- Daily scheduled scans
- Everything in STARTER, plus:
- API Key & Secrets Detection (prevents $10K+ bills)
- Rate Limiting & DDoS Protection testing
- Subdomain Takeover detection
- API Security analysis
- Broken Access Control (IDOR) testing
- Mixed Content detection
- PDF reports
- Email alerts and webhooks (coming soon)
- Priority support (24h response)
One Vulnerability Can Cost Everything
All it takes is a single weak spot a missing header, bad CORS rule,exposed endpoint, or outdated dependency — for attackers to break in. The result? Data leaks, downtime, lost trust, and costly damage. Attackers only need one mistake. You can't afford to miss it.
